| Home | Services | About Us | Reference Area | ||||||||
Configuring WFAS, dual NIC on Server 2008 R2, Quick Guide |
||||||||
|
Quick guide to configuring WFAS and NLA on a multi-homed (dual NIC) Windows 2008 R2 server.
For an in-depth investigation to several configuration options, see the Multiple NIC, Configure Windows Firewall with Advanced Security page. This page is intended to by our own internal use Quick Guide. Use this information at your own risk. This guide solves the problem in Server 2008 R2 of assigning multiple NIC's different Windows Firewall with Advanced Security (WFAS) profiles. This way, you will be able to assign in Network Location Awareness (NLA) a "Public Network" profile to a publicly connected network, and assign a "Private Network" profile to a privately connected network. This information should also apply to Windows 7, but this has not been tested. Backup the un-touched WFAS settings. In the WFAS tool left pane, right-click 'Inbound Rules' choose 'Export List...'. Save the text file to the documentation directory. Configure so LAN network can be assigned 'Private network' profile in NLA. This information presumes that the LAN IPv4 settings do not have a gateway (only the WAN has a gateway), and therefore NLA was not able to identify the LAN network. Preferred method: Make the LAN network identifiable by NLA. For the LAN NIC properties, configure the IPv4 Advanced DNS settings for "DNS suffix for this connection:" to match the (fully qualified) Domain Name for the LAN. You will probably need to restart the NLA service for the LAN network to now be identified. Note: if the network name associated with the LAN connection is still "Unidentified Network", then NLA did not correctly identify the LAN network.
For a stand-alone server, the procedure is: 1. From Command Prompt: gpedit.msc 2. Browse: Computer configration --> Windows Settings --> Security Settings --> Network List Manager Policies --> Unidentified Networks 3. Change 'Location type' to: Private, click 'Ok'.
Change WFAS with VBScript Due to the gaping holes with default WFAS settings, and because it would be very tedious to change all of the WFAS rules individually, use the following scripts to lock-down all ports associated with the "Public Network" profile (except Remote Desktop). Note: Sample scripts here are ".txt" files, save them as ".vbs". Disclaimer: Use sample scripts at your own risk! You should export current WFAS settings first! To accomplish "allow RDP only" for the "Public Network" profile, use the VBScript: Change all "enabled" rules with "Profile=All" to "Profile=Domain,Private". To allow ICMPv4 response to Ping (no default rule, so this needs to be added) use the VBScript: "add rule to allow ICMPv4 ping". References: See the Multiple NIC, Configure Windows Advanced Firewall page. |
||||||||
| Copyright © 1996-2025 Ohman Automation Corp. All rights reserved. | ||||||||
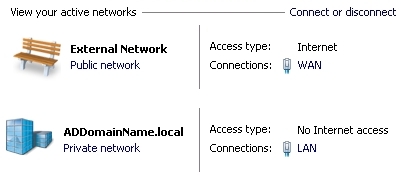 Tweak NLA Configuration:
Tweak NLA Configuration: